Every little bit, a new case of malicious attack constantly comes to our ears and it's not just big companies that are in the crosshairs of hackers. According to the FBI*, cybercrime increased by 300% in 2021 and the World Economic Forum** stated that cyberattacks are one of the most significant risks to corporations worldwide.
EY Global*** consultancy heard from 1000 cybersecurity executives and 43% of them stated that they have never been more concerned about cybersecurity than they are now and their ability to deal with threats. We all agree that it is difficult to define which front to attack first, as cybersecurity executives must still work to ensure systems that are resilient and support ongoing digital transformations.
We know you need to increase cyber surveillance, reduce the attack surface, increase visibility and protect workloads. It is necessary have consistent security for workloads running in virtualized, private, and hybrid cloud environments, generate prioritized vulnerability reports, and rely on prevention, detection, and response capabilities. It is a lot and demands a budget that is not always available. What to do?
face the problems
We have seen a growing increase in ransomware attacks, with great detriment to businesses. They had antivirus and various cybersecurity solutions, but hackers are increasingly sophisticated in their attacks. When we study the victim companies more deeply, we see that they have several problems in common and the three main ones are:
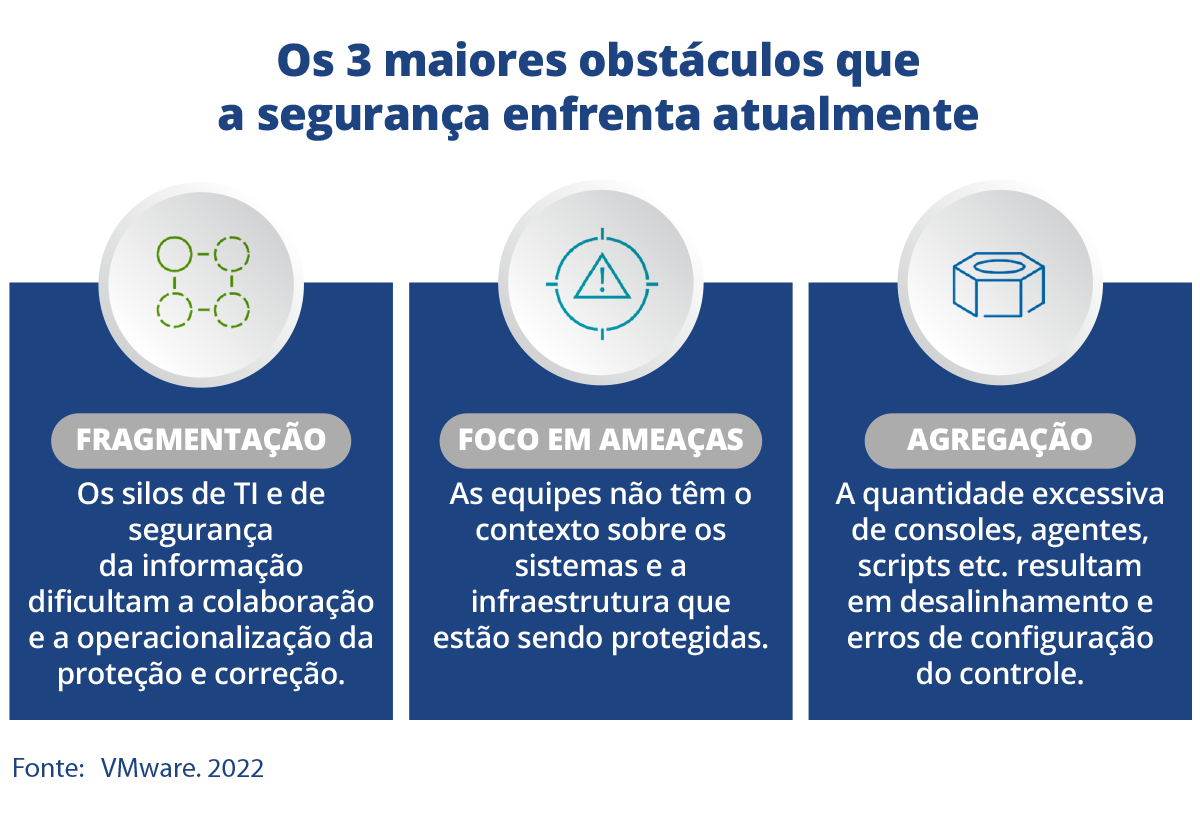
Start tackling cybersecurity issues by looking inside your company, making a diagnosis of how these 3 topics affect your day to day. Do IT areas work separately? Lack real-time visibility? Are there excess applications and high complexity?
The rapid growth of the attack surface, based on containers and ephemeral workloads, requires security to be consolidated into a unified platform. You can no longer react to threats with unitask products. IT Operations, SecOps, and DevOps teams need to join forces, work with shared, real-time visibility into workloads and containers, and focus on vulnerabilities prioritized by risk.
Wide sight
To work, cybersecurity must be viewed broadly. That's why our approach has been Intrinsic Security, which enforces requirements without increasing complexity, taking into account endpoints, workloads, networks, workspaces and clouds.
The approach is intelligent, automated and integrated. We leverage infrastructure and control points in a new way, spanning any apps, clouds or devices. This enables the company to have robust cybersecurity, capable of identifying risks and preventing them, detecting threats and reacting quickly.
Cybercrime has a great impact on companies, with financial and image losses. Therefore, cybersecurity cannot be seen as an expense, but as a business strategy. It is no longer a matter of care, but a duty of loyalty to consumers and partners who have entrusted their data to an organization that cannot be vulnerable.
The LGPD (General Personal Data Protection Law) is in force, with countless ongoing processes that require compensation for damages resulting from data leakage. It is necessary to act preventively, quickly and intelligently, with appropriate solutions.
Our technical team is at your disposal and VMware solutions provide integrated and efficient security for any device, network and cloud. VMware gives you the freedom and control you need to drive business forward in the multicloud age.
SOURCES:
* FBI Report Finds 300% Rise in Cybercrime Due To Pandemic (techzone360.com)
** World Economic Forum sees cyber as high risk (cisoadvisor.com.br)
*** Cybersecurity: How do you rise above the waves of a perfect storm? | EY – Global



